Nmap (“Network Mapper”) is a free and open source (license) utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service up-time.
Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
It was
designed to rapidly scan large networks but works fine against single hosts. Nmap runs on all major computer operating
systems, and official binary packages
are available for Linux, Windows, and Mac OS X.
Let's check out the basic nmap command in our day-to day life.
Host Scan
Host scan is used by penetration tester to identify active host in a network by sending ARP request packets to all system in that network. As result it will show a message "Host is up" by receiving MAC address from each active host.
Syntax: nmap -sP <target IP range>
nmap -sP 192.168.29.124
From given below image you can
observe result of response generated by nmap for active host.

Port scan / TCP scan
If penetration testers want to identify open or close state of a particular port on target machine, then they should go with nmap port scan.
Port Status: After scanning, you may see some results with a port status like filtered, open, closed, etc. Let me explain this.
Open: This indicates that an application is listening for connections on this port.
· Closed: This indicates that the probes were received but there is no application listening on this port.
Filtered: This indicates that the probes were not received, and the state could not be established. It also indicates that the probes are being dropped by some kind of filtering.
Unfiltered: This indicates that the probes were received but a state could not be established.
Open/Filtered: This indicates that the port was filtered or open, but Nmap couldn’t establish the state.
Closed/Filtered: This indicates that the port was filtered or closed but Nmap couldn’t establish the state.
nmap -p135 192.168.1.127
Above command will try to connect with port 135 as result if port is open then it will display state “open” as
well as “service” running on that particular port.

Using port range scan, you can scan a particular range of ports of target network as per your requirement.
nmap -p1-1000 192.168.29.124
Above command will perform scanning from port number 1 to till port number 1000 and identify the state and service for open ports.
ALL Ports
If penetration testers want to
scan all 65535 ports; then they should execute given below command which will enumerates
the open ports of target system:
Syntax: nmap -p- <target>
Above syntax is used for scanning all ports of target network, keep patience while executing above format because it will take some time to enumerate open port, or you can also execute given below command which uses parameter “–open” to perform same task in order to save time.
nmap -p1-65535 192.168.29.197 --open

UDP Scan
UDP services are mostly ignored during penetration tests, but fine penetration testers know that they often expose host essential information or can even be vulnerable moreover used to compromise a host. This method demonstrates how to utilize Nmap to list all open UDP ports on a host.
Syntax: nmap –sU <target>
nmap -sU 192.168.29.197
From given below
image you can observe
the result for UDP port scan.

Apart from open port enumeration nmap is quite useful in OS fingerprinting. This scan very helpful to penetration tester in order to conclude possible security vulnerabilities and determining the available system calls to set the specific exploit payloads.
Syntax: nmap -O <target>
nmap -O 192.168.29.197

Version Scan
Version detection helps you obtain this information. Fingerprinting a service may also reveal additional information about a target, such as available modules and specific protocol information. Version scan is also categories as “Banner Grabbing” in penetration testing.
Syntax: nmap -sV <target>
Following command will dump the result for installed version
of running services
of target’s machine.
nmap -sV 192.168.29.197

Aggressive scan
This option enables additional advanced and aggressive options. Presently this enables OS detection (-O), version scanning
(-sV), script scanning (-sC) and traceroute (–
traceroute). This option only enables features, and not timing options
(such as -T4) or verbosity options
(-v) that you might want as well. You can see this by using one of the following
commands:
Syntax: nmap -A <target>
nmap -A 192.168.29.124
If you will notice given below image, then you will
observe that the result obtain
by it is
the combination of multiple scans.
As its dump “version” of running application, “OS fingerprint”, “traceroute” and “host script scanning” which is
showing some very essential information related to host system.

Stealth Scan
SYN scan is the default and most popular scan option for good reasons. It can be performed quickly, scanning thousands of ports per second on a fast network not hampered by restrictive firewalls. It is also relatively typical and stealthy since it never completes TCP connections.
The port is also considered open if an SYN packet (without the ACK flag) is received in response.
This technique is often referred
to as half-open scanning because you don’t open a full TCP connection. You send an SYN packet as if you are going to
open a real connection and then wait for a response.
An SYN, ACK indicates the port
is listening (open)
nmap -sS -p 22 192.168.29.197

Fin Scan
A FIN packet is used to terminate
the TCP connection between the source and destination
port typically after the data transfer is complete. In the place of an SYN packet, Nmap starts a FIN scan by using a
FIN packet. If the port is open, then
no response will come from destination port when FIN packet is sent through
source port.
nmap -sF -p 22 192.168.29.197

Null Scan
A Null Scan is a series of TCP
packets which hold a sequence number of “zeros” (0000000) and since there are none flags set, the destination
will not know how to reply the
request. It will discard the packet and no reply will be sent, which indicate
that the port is open.
Type following NMAP command for
TCP scan as well as start Wireshark on another
hand to capture the sent Packet.
nmap -sN -p 22 192.168.29.197

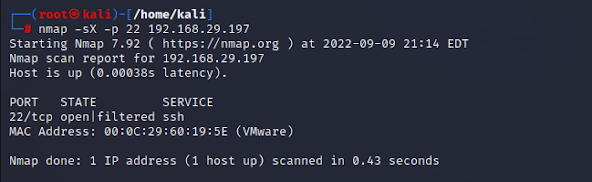
Xmas Scan
These scans are designed to
manipulate the PSH, URG and FIN flags of the TCP header, Sets the FIN, PSH, and URG flags, lighting the packet up like a
Christmas tree. When source sent FIN,
PUSH, and URG packet to a specific port and if the port is open then destination will discard the packets and will
not send any reply to the source.
Type following NMAP command for TCP scan as well as start Wireshark on another hand to capture the sent Packet. From the given image you can observe the result that port 22 is open.
Conclusion
In this blog we have seen the most popular nmap commands, most of these commands are used in daily purpose. Mostly Network engineers, Cybersecurity researchers, Penetration testers are using this types of commands. Also there are lots of other commands are also available, you can access all those by using nmap --help commands and you will get all the list of Nmap commands and the also explain how to use them.
The alternate application are also available such as Zenmap, but zenmap is using graphical user interface and Nmap is using command line injection. It's upto you which application you want to use.
Keep learning and keep exploring!


Comments
Post a Comment
If you have any doubts. Please let me know.